Taking Back What Is Already Yours: Router Wars Episode I

I have been living in my current apartment for more than a year now and I noticed I have never inspected my router which was provided by my ISP when I moved in. The only thing I changed in router is the default login password(admin/password) to the web interface. So I decided to take a more detailed look.
It is an Huawei HG253s router and is widely used by Turkcell Superonline customers since it comes with the internet plan. Actually, Turkcell Superonline enforces the use of these modems by not allowing devices whose MAC addresses are different than these pre-registered Huawei routers. It is possible to do a MAC cloning with another router but still you need to buy one of these pre-registered Huawei routers to learn a legit MAC address.
The first thing I did was initiate a fast nmap scan on the router to see if there is open ssh or telnet port.
1 | $ nmap -F 192.168.1.1 |
We can see that there is an ssh port open. So let’s try to connect with admin user:
1 | $ ssh admin@192.168.1.1 |
This is an unexpected response. The router offers legacy diffie-hellman-group1-sha1 key exchange method. According to this openssh page:
OpenSSH supports this method, but does not enable it by default because is weak and within theoretical range of the so-called Logjam attack.
But we can enable it with KexAlgorithms option. So let’s try again:
1 | $ ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 admin@192.168.1.1 |
Again another legacy offer. Let’s enable the cipher and connect again:
1 | $ ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 -oCiphers=+3des-cbc admin@192.168.1.1 |
Now it asks password but what is it? I tried the default password(superonline) and the password I set to the web interface with no luck. After a little bit search on the internet I found out there is another user called Root(surprise!) goes by R8Ibq_2K15Gna as the default password for my firmware version HG253sC01B039. One more time then:
1 | $ ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 -oCiphers=+3des-cbc Root@192.168.1.1 |
It worked but I don’t know what ATP Cli is. Again after a little bit of search on the internet reveals it is some kind of control/test interface that should respond to some commands. I tried some commands but only help returned a response.
1 | ATP>shell |
We know it is responsive since it returned a response to help command but it is obviously highly restricted. I tried to find my version of the firmware (which is the latest one by the way) to get my hands on this ATP Cli binary but it turned out that neither Huawei nor Turkcell Superonline has published any version of the firmware. It is very unusual. There should be an upgrade mechanism since I know there are routers running older firmware. So I decided to sniff my router’s network.

In order to achieve this, I gathered two USB-ethernet convertors and my debian laptop. I will use bridge-utils and a network sniffer’s favorite tool: Wireshark. To create a bridge, run:
1 | brctl addbr br0 |
Then bond interfaces to the bridge:
1 | brctl addif br0 eth0 eth1 |
Disable multicast snooping
1 | echo 0 > /sys/devices/virtual/net/br0/bridge/multicast_snooping |
And run wireshark on eth0 or eth1. Note that both interfaces are in promiscuous mode.
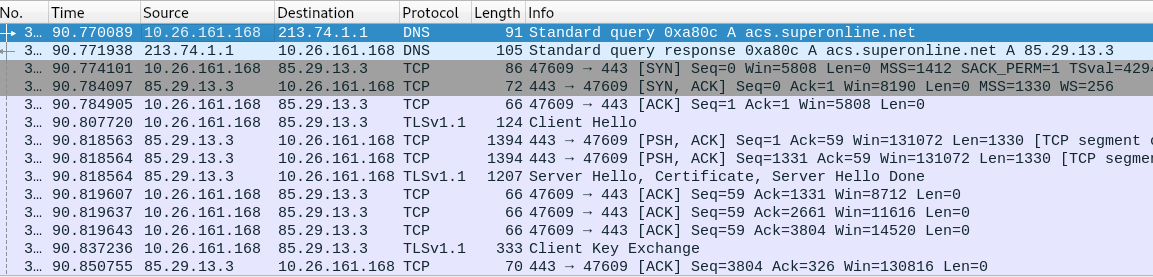
Interesting! After initializing PPPoE session, we can see a DNS query is made for acs.superonline.net and a TLS connection made to that IP address. Due to the nature of TLS connections, it isn’t possible to see the content of the communication but we can assume the router uses TR-069 protocol since ACS most probably stands for Auto Configuration Server which is an element of this specification. And better than that, probably it is used to upgrade firmware thus we may sniff it over the air.
This is the end of first part. In the next part, I’ll try to sniff the communication between acs.superonline.net and my router and also modify it if it’s applicable/necessary.
Note: The main discussion about these post series is here.