Taking Back What Is Already Yours: Router Wars Episode II
In the previous post, we’ve learned that our router is connecting to acs.superonline.net and we assumed it’s an Auto Configuration Server. Since it was a TLS connection, we couldn’t see the details of that communication.
There isn’t any known attack on TLS v1.2 which our router is using. So the first thing that came in my mind is to check if there is a plain HTTP version of acs.superonline.net. I ran a nmap scan expecting port 80 will be open:
1 | $ nmap --open acs.superonline.net |
Port 80 isn’t open but curl requests to open ports returned the same length, same header responses so probably the same server (or test server) is running on these ports. Also port 8010 uses plain HTTP so maybe if we could change ACS URL to 8010 we could sniff the communication. I looked into the web interface of the router to see if there’s a configuration page for TR-069 but no luck there. I decided to reset the router to its factory settings to check if https://acs.superonline.net is indeed hardcoded in the firmware and lucky for me the router made a plain HTTP connection to a new port of acs.superonline.net: port 8015! I can read all requests with wireshark now and they’re indeed TR-069 requests.
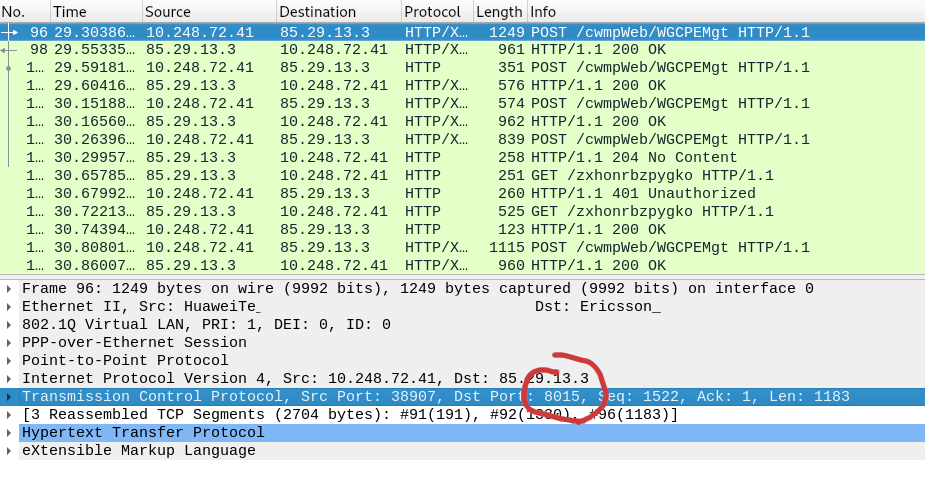
Before diving into these requests, I want to give some information about TR-069 protocol. TR-069 is mainly used by Internet Service Providers to configure your modems/routers remotely. It’s possible to set passwords, configure Wi-Fi, even upgrade firmware via TR-069 protocol. Here is a crash course about TR-069(source). So basically it’s a backdoor your ISP installed in your router! And unlike most of the other routers, in HG253s it isn’t possible to disable TR-069. This is very invasive and unacceptable. It may seem necessary to apply security patches published by your ISP but the user should be able to disable it whenever she wants.
Okay, let’s look into the communication between HG253s and my ISP’s Auto Configuration Server. The requests are exchanging information and mainly like the one below:
1 | POST /cwmpWeb/WGCPEMgt HTTP/1.1 |
But in all these requests, there’s an important one coming from ACS:
1 | <soapenv:Envelope xmlns:soap="http://schemas.xmlsoap.org/soap/encoding/" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:cwmp="urn:dslforum-org:cwmp-1-0" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> |
Yep, it’s changing the ACS URL to TLS enabled version. So if we do a MitM attack and force router to keep the URL same, we can sniff latter requests too. Even if we can’t, we can provide an invalid URL and disable TR-069 requests. MitM attack should be easy on linux with all that native networking support like iptables, ebtables and bridges(!).
I ran BurpSuite on port 8080 with transparent proxy and then I executed the script below with bridge already set(see my previous post:
1 |
|
Note that you need br_netfilter filter module enabled. Normally, ebtables work at ethernet layer and ignore the layers above but with br_netfilter and /proc/sys/net/bridge/bridge-nf-call-iptables enabled, it’s supposed to call iptables from ethernet layer. This is how iptables and ebtables work together:
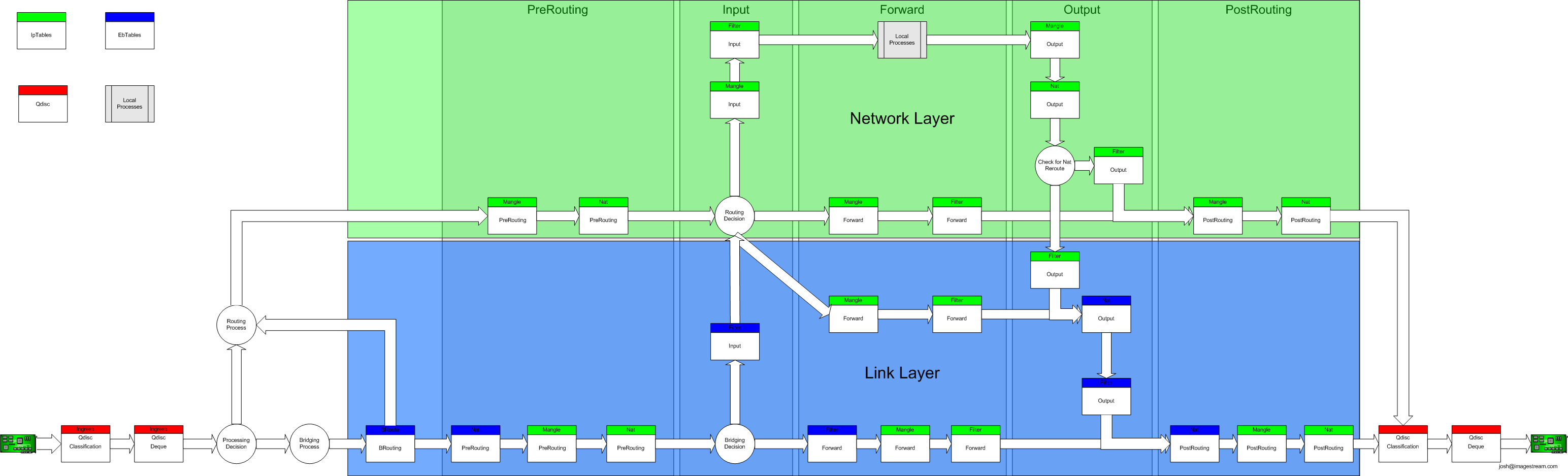
Let’s go over our code line by line:
1 | ebtables -t nat -A POSTROUTING -o eth0 -j snat --to-source $ISP_MAC |
The above code changes source MAC addresses of packets in case they’re coming from BurpSuite. For example if a packet going through eth1 interface(going to wild), it’s source MAC address should be router’s MAC address. See previous post for the setup.
1 | iptables -i br0 -t nat -A PREROUTING -p tcp -d $ACS_IP --dport $ACS_PORT -j REDIRECT --to-port 8080 |
This is a simple redirection rule for packets whose destinations are acs.superonline.net:8015.
1 | iptables -o eth1 -t nat -A POSTROUTING -p tcp -j SNAT --to-source HUAWEI_IP |
This does the same thing we do with ebtables rule but in the IP layer.
And it didn’t work. Yeah. It worked perfectly fine in my LAN but it didn’t work outside of my router. After many hours of debugging and a few stackoverflow questions later, I figured the packets follow PREROUTING(ebtables) -> FORWARD(iptables) -> POSTROUTING(ebtables) chains but never visit iptables PREROUTING and POSTROUTING chains. I think it’s because of the implementation of br_netfilter module for PPPoE layer but I still don’t have the definitive answer.
I decided to implement the bridge and iptables redirects myself. First I looked at how iptables redirects work. Apparently when redirecting a packet, iptables set SO_ORIGINAL_DST value so that the transparent proxies would know the original destination of the packet. At user space you have permission to read but you don’t have permission to set this value. Since all I want to change the ACS URL parameter, I decided to make packet modification a part of my code.
My choice of language for this task was go because I wanted to practice go and also goroutines are very useful for this kind of multi-threaded code.
You can reach my code here. I won’t go line by line over my code but I want to talk about the logic flow and problems I’ve encountered while writing.
First of all, outgoing means the packet is coming from the router and going to the wild. Incoming means vice versa. And interfaces are referred as ports (like in outgoingPort).
There are three main functions. The first one is:
1 | func bridge(outgoingPort BridgePort, incomingPort BridgePort, label int) |
What it does is this: it reads packets coming to outgoingPort then forward to incomingPort. Two instances of this function are running for both directions. I use gopacket/pcap to read/write packets. The problem is while reading from the handle you receive assembled packets. For example, you don’t get tcp fragments of a HTTP packet, you get a complete HTTP packet. And this is a problem while writing to the forwarding handle because the packet size shouldn’t exceed the interface MTU. So I needed to implement a fragmentation function that divides packets into sizes smaller than MTU and arranges TCP sequence numbers accordingly.
The other problem I had is caused by my Asus ethernet-usb3 converter. It was appending two extra random bytes to the end of each packet! It took many hours to figure out why I was having length issues. This is how it is seen in wireshark:
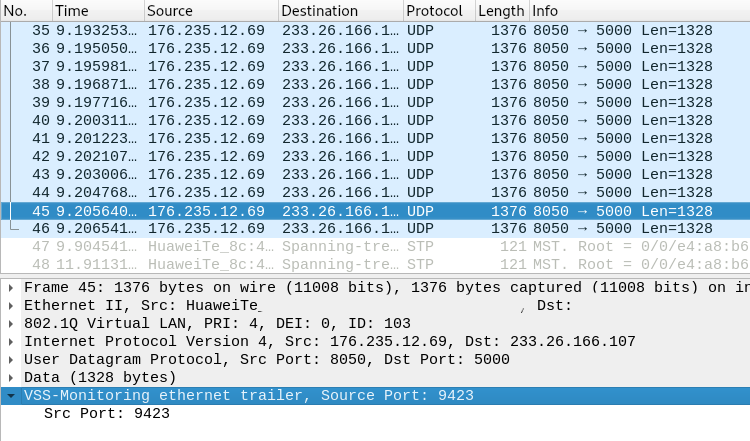
After searching on the internet, I found out that they’re some kind of debug bytes. So I simply started to strip out those two extra bytes I read from Asus converter.
1 | if label == INCOMING { // strip out vss-monitoring trailer |
The other two important functions are
1 | func processIncoming(packet gopacket.Packet) ([]byte, error) |
and
1 | func processOutgoing(packet gopacket.Packet, wholePacket bool) ([]byte, error) |
Both functions are called from bridge if packets are going to or coming from acs.superonline.net:8015
1 | if label == OUTGOING && bytes.Equal(ip.DstIP, []byte{85, 29, 13, 3}) { |
processIncoming’s duty is to replace https://acs.superonline.net in TR-069 packets from ACS with whatever I want. For now, we want it to replace with http://acs.superonline.net:8015.
On the other hand, processOutgoing’s duty is to replace the firmware version to something lower than my router has. So that way, maybe we can trick ACS to send the latest firmware.
When I did a factory reset and ran the MitM code, the only different thing happened is that the router started to send periodic inform messages in addition to usual information exchange requests. No firmware upgrade, no password set request. My internet connection is even gone since the PPP credentials aren’t hardcoded in the router.
Before without my touch, the router connects to ACS on port 8015, then ACS sends a new ACS URL along with username and password and finally the router connects to this new URL. Maybe we shouldn’t keep the URL same; we should change it to force the router to initiate a new session. But have can we achieve that without switching to HTTPS URL? Remember, we already found another HTTP port running at 8010 in the beginning of this post. So let’s try replacing https URL with that one.
And voila!
1 | <soapenv:Envelope xmlns:soap="http://schemas.xmlsoap.org/soap/encoding/" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:cwmp="urn:dslforum-org:cwmp-1-0" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> |
We received password update for Root user! And a few requests later:
1 | <soapenv:Envelope xmlns:soap="http://schemas.xmlsoap.org/soap/encoding/" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:cwmp="urn:dslforum-org:cwmp-1-0" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> |
We got firmware link and it’s reachable from everywhere! To sum up, now we got the latest unpublished firmware and the password for Root user. In the next post we’ll see what we can do with these.
Note: The main discussion about these post series is here.